1 like
3 likes
1 like
2 likes
post more takes buddy boyo... i am curious how much more aligns with my own worldview
2 likes
2 likes

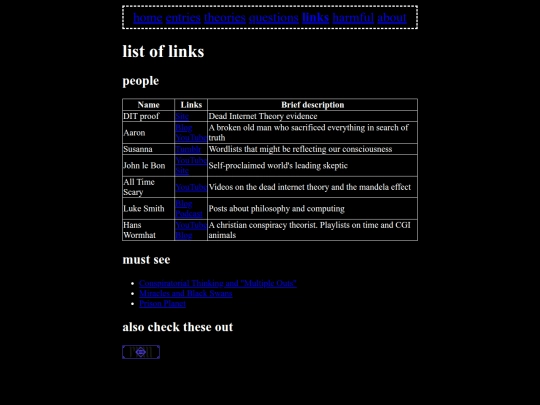








regarding RNG, most implementations are actually PRNG which use an entropy source in combination with tricks like the modulus operator. if you know the seed of a PRNG it is deterministic. but the seed itself may or may not be random. secure cryptography may utilize other sources of randomness like mouse input, etc.